Messages
That Travel
Through
Physical Space
$3 devices. 60-day battery. No towers, no internet, no accounts. The network is the people who carry it.

When towers fall, when power fails, when the state decides who may speak — information still moves. At walking speed. Carried by hands.
After the Storm
Cell towers down. Power severed for miles. First responders move through wreckage, dropping $3 devices from the window. Each one becomes a node. Information moves at the speed of boots on rubble.
Mesh nodes operate independently — no towers, no grid, no internet backhaul required.
200km to a Signal
People already travel between villages — on foot, by bus, by bicycle. The network doesn't build new routes. It follows the ones that already exist, carried in pockets alongside grain and medicine.
Delay-tolerant by design. Messages travel hours or days, arriving when carriers arrive.
No Servers to Subpoena
No accounts. No metadata. No timestamps on a server. The network leaves no trail that scales — surveillance requires physical presence at every node, every path, every pocket.
Location-gated encryption. No identities, no logs, no central point of compromise.
Below the Threshold of Control
The internet goes dark. A $3 device buried in a garden wall carries testimony that outlasts the siege. When the network is the people, shutting it down means stopping every pair of feet.
Too cheap to suppress, too distributed to surveil, too simple to break.
No servers. No logins. No logs.
Just physics.
The technology is simple. Three devices. Three hops.
Three Hops
Someone writes. Someone walks. Someone receives. No towers required.
Drop
You hold your phone to a small device hidden in your neighborhood. Your message is encrypted on contact and stored inside. This is a Throwie.
Carry
Someone walks past with a phone in their pocket. The message jumps to their device automatically — no app to open, no action to take. They are a Mule.
Surface
When a carrier passes a bridge point, the message reaches the wider world. Hours later. Maybe days. It arrives because someone walked. This bridge is a Sink.
The Hardware
Three device classes form the physical backbone of the mesh
Throwie
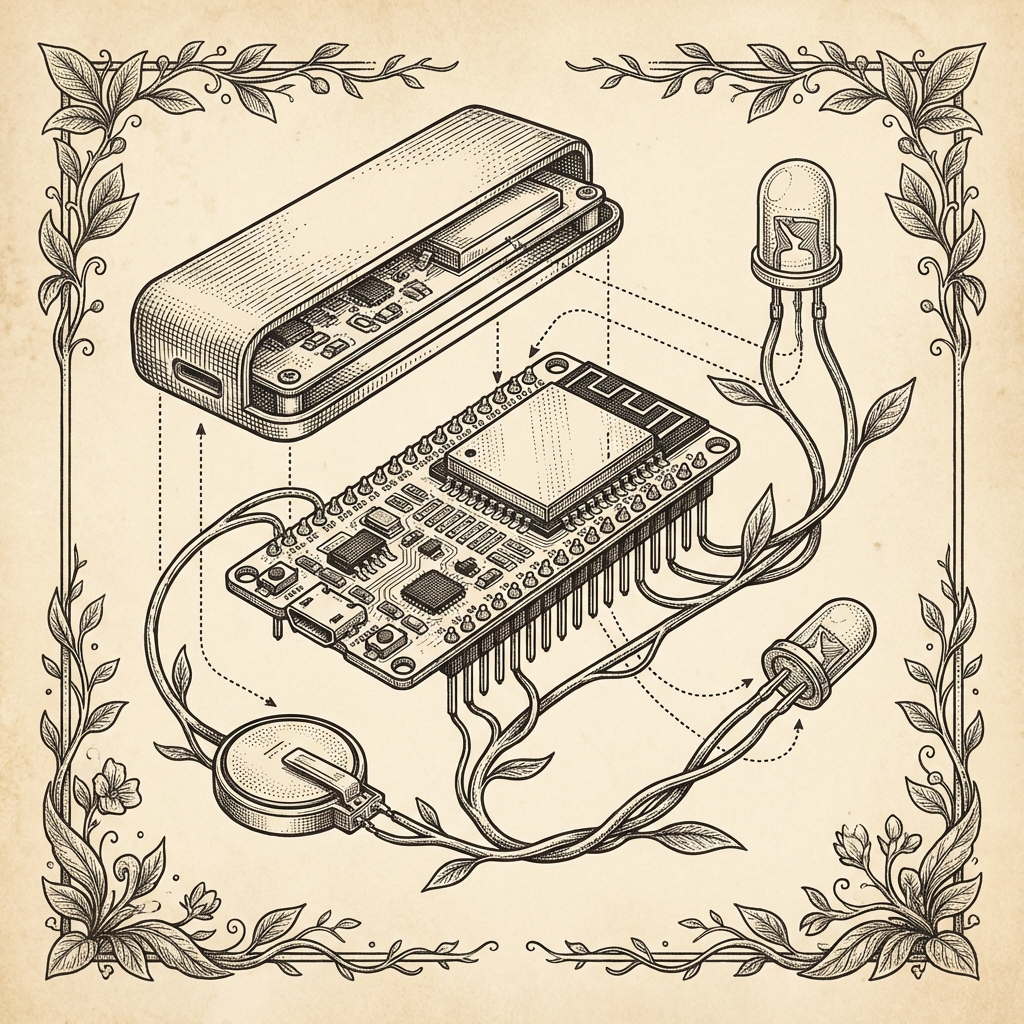
ESP32-C3 on a LiFePO4 cell. Costs $3. Sleeps 60 days on a single charge. Holds 750 messages.
Mule
Mobile relay app. Ferries messages between nodes without internet. Zero config.
Sink
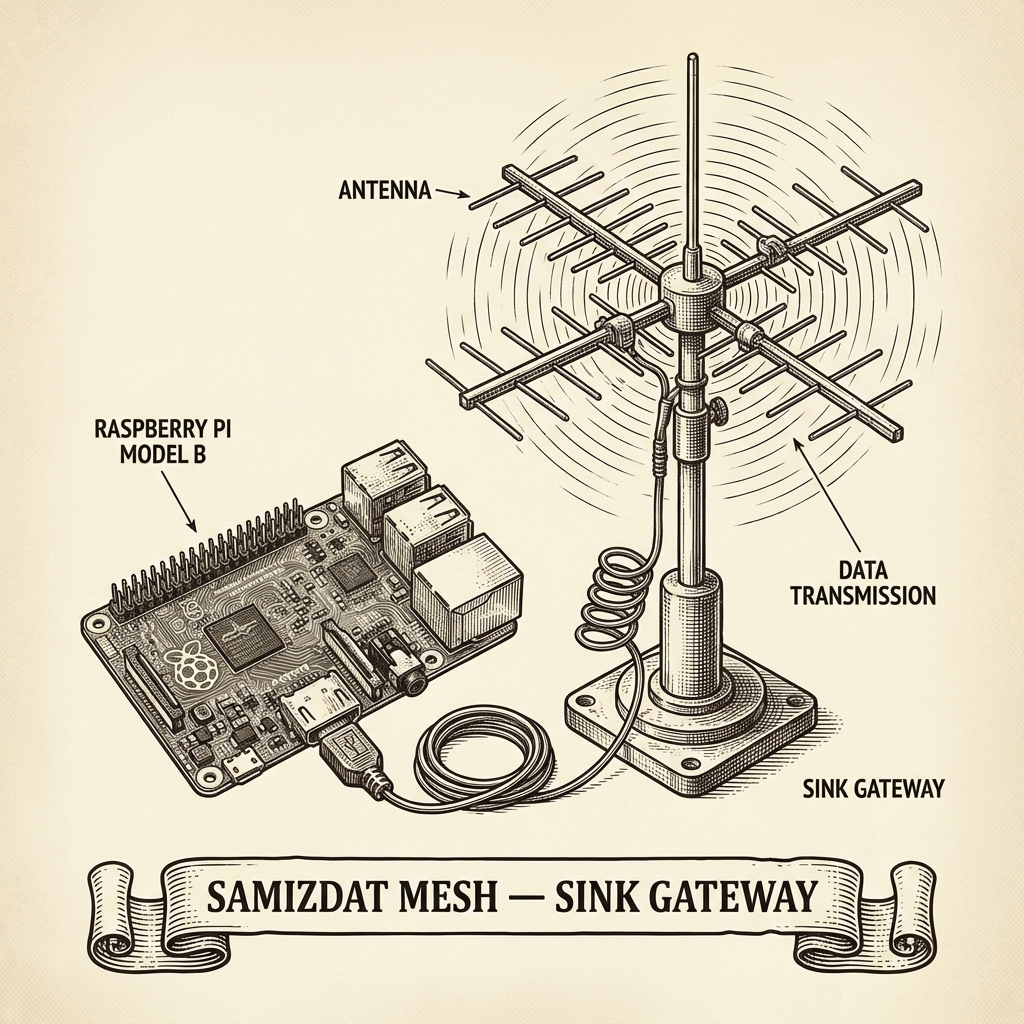
Raspberry Pi running a lightweight bridge. Collects messages from passing carriers and publishes them.